
BEC – The most expensive email your company may ever get
Business Email Compromise (BEC) costs organisations globally a staggering amount of money, but there are some simple steps you can take to put a stop to it.
For a relatively simple attack, Business Email Compromise (BEC) costs organisations globally a staggering amount of money. The FBI estimated it has funnelled $26bn into the pockets of cyber criminals in the three years to July 2019. This is more than the GDP of Iceland.
What is Business Email Compromise?
In essence, Business Email Compromise is when an attacker pretends to be someone they aren’t on email, typically senior management, to achieve their own ends. This is usually convincing a person to divert funds into a different account or tricking them into sharing sensitive databases or IP. In this way, a single email can cost tens of thousands.
There are two main types of BEC attacks, those which use a compromised email account and those which come from a spoofed email address, aiming to look like they originate from a specific individual at a legitimate domain.
To carry out the first kind, the attacker will need to compromise the email account of an important person inside the target company. Mass migration onto platforms such as Micrsoft 365 has made this easier, putting a fresh set of user credentials for the CEO or CFO just a phish and a fake login page away.
Once the attacker has the requisite username and password, they sit quietly in the background watching and learning who does what and how the owner of the hijacked account communicates before striking.
Less advanced Business Email Compromise attacks work in a similar way but instead of the request originating from a senior team member on your mail server, they use a ‘nearby’ or ‘cousin’ domain. For example, janedoe@acmeecorp.net instead of janedoe@acmecorp.com.
What to watch out for
The quality of such Business Email Compromise attacks varies, with more detailed ones spending significant time collecting target info and intelligence and using these in their fake emails. As it could net the attacker a significant amount of money if successful – it is typically better thought through than your run-of-the-mill 419 scammer or mass phish. The image below sums up some of the social engineering techniques typically used.
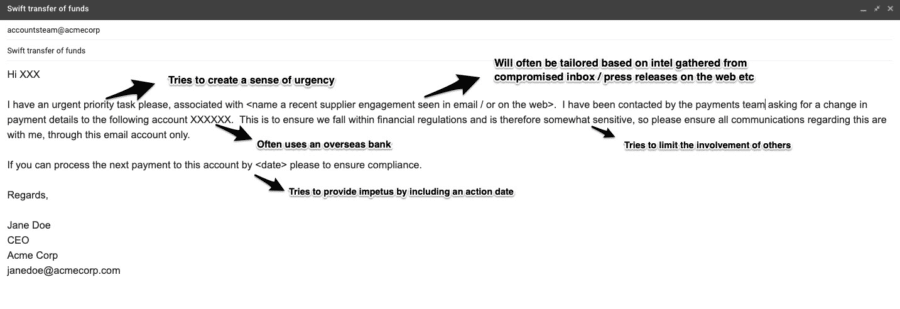
How to protect yourself
As with most cybersecurity issues, it is a hybrid human/technology problem.
To help protect against the human risk elements involved, training against up-to-date phishing scams to teach people to question emails is vital. Carrying out the actions of senior management is hardwired in most employees.
It is important to break this chain by having employees associate requests to suddenly authorise unplanned transactions or send valuable corporate assets with high risk and challenge accordingly. This education needs to be done regularly and in an environment that encourages such challenges to senior staff, rather than attaching a stigma to them.
Implementing a process to consider manual approvals for payments above a set threshold should also be considered.
Your email security solution is the front-line of defence. Make sure it has the multiple layers necessary to address the variety of elements of BEC. This includes features to quarantine and drop emails and executive tracking capabilities to identify real names in multiple address fields.
Integrated domain name and IP risk scoring is also a valuable countermeasure, the smart security team could also consider purchasing nearby domains to prevent their use in attacks. Finally, an email solution which can intelligently categorise and analyse the content of emails in context is also valuable.
Multi-factor authentication (MFA) can also play a part in mitigating the Business Email Compromise issue. It will hamper any attacker with a stolen username and password details, stopping them from the kind of multiple illegitimate logins that allow for the collection of strong target intel.
Additionally, while these attacks originate inside email, they often encourage the victim to take actions in other applications. For example, encouraging people to email data from Salesforce or documents from a cloud storage app, which is why a solution which can see and mitigate across the kill-chain is vital.
In organisations of all sizes, the management burden of staying ahead of these variables can be alleviated by automated security. This is the ethos behind our Autonomous Security Engine – ASE.
Whilst technically relatively simple, Business Email Compromise is growing as an issue because it exploits human frailties with the potential for a big return for attackers. However, taking the steps outlined above and will make it far harder for this to happen.
Make a start by downloading the BEC Checklist. For more practical, actionable insights and guidance on securing your organisation from threats such as Business Email Compromise, particularly when using Microsoft 365, visit Defence365.
Defence265 Vlog: How to protect your organisation from advanced email threats